When building software storing passwords as plain text is a bad idea. Storing passwords as plain text means you store the exact text your user has typed into the input filed within your application. This approach is as unsecure as you can get - anyone with access to your database (authorised or unauthorised) can simply view passwords and copy them.
A better way to store passwords securely is to use a hashing technique before saving a password to the database. Hashing performs a one-way conversion on a piece of data transforming it into another relatively short piece of data. By one way we mean that it is very difficult, in fact practically impossible, to reverse it and find the initial piece of data from the resulting "hash".

Storing passwords as hashes in the database means that if someone does get access to where your passwords are stored they will not see the password that the user enters for authentication. Great you say, my password is secure! Not so fast.
If a malicious individual does get access to a list of hashed passwords they could use Rainbow tables to generate a list of hashes for common words or passwords and compare their resulting hashes with the hashes of your users passwords. Finding a match would allow the malicious individual to exploit that user’s password.
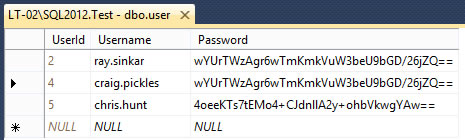
For example, in this table there are three user’s in the database, two with the same hashed password. In this example I am Craig and I know my password is “password123” and I can see that my hash matches Ray's, I can therefore ascertain that Ray’s password is also “password123”
So what can be done about this problem - just add some salt!
"Salting" a password is the solution used to hash more than just a user’s password. Instead of just hashing a user’s password we hash a concatenation of their password and a unique "salt" value. We store the salt value alongside the password so that we can regenerate the hash with the user’s password again at a later date.
This table shows the same users and their passwords, as well as their salt values.
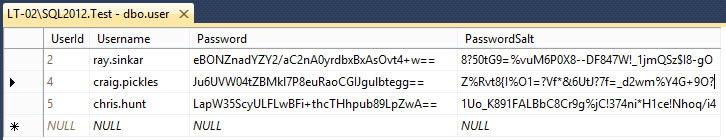
We can see here that we can no longer easily determine that Craig and Ray’s passwords are the same. Similarly now if a malicious user were to compare the hashes to hashes generated in a simple Rainbow table it would not be possible to identify any user’s passwords.
A malicious individual could still generate a table of hashes for each salt value however we have made it a lot harder for them, and thus not efficient for them to try and take on recovering the passwords from the hashes.
Cryptology is a complicated subject area and there are constant developments and new research happening all the time.
With enough time and computing power it is impossible to truly say any password is 100% secure however hopefully this post gives you an understanding of some of the techniques that can be used to securely store passwords.